About single sign-on
Single sign-on (SSO) allows to connect user base in CRIBWISE system with users managed in external identity provider, typically customer’s own provider of user identities. It allows the customer to manage their users centrally and force the same login policies as demanded from users when working with internal systems. For users, this setup brings advantage of using the single login credentials and necessity to login only once while using several systems.
How SSO works in CRIBWISE
Once SSO is activated, navigating to address of Admin Portal will redirect user to login screen of the external identity provider. User must successfully proceed the authentication flow with the external provider (including multi factor authentication, if such is required). Once user is successfully authenticated, it is redirected to Admin Portal for authorization. To successfully pass authorization in Admin Portal, user must exist in the Admin Portal with email address matching the authenticated user and it must have privilege to access the Admin Portal (must belongs to user group with role AP users). While user is logged in Admin Portal, all restrictions set for this user in Admin Portal’s user and user group management will be applied.
While the SSO is active, it is not possible to login to Admin Portal using only username and password defined in Admin Portal’s user management.
SSO is utilized for login to Admin Portal only. Login to Shop Floor Interface, users defined in the Admin Portal must be used (with role SFI users), authentication must be performed via login name and password or via external accessory (RFID card, barcode, Coges key). It is still possible to login via account administrator (from Customer Management Portal) even when SSO is active. To prevent login for these, change access control settings.
Setup the SSO with Azure AD
Before SSO can be activated, all users in Admin Portal must have a unique email address. If there are two or more users with the same email address, activation of SSO will not be allowed. Ensure this prerequisite before proceeding to next steps. Following steps describes how SSO can be setup between CRIBWISE and customer’s own Azure Active Directory. Common setup of the Azure AD is not in scope of this manual, please refer to Microsoft documentation. As a first step, ensure, that users which should login into Admin Portal exist in the portal and have email address matching with principal name of user from Azure AD.
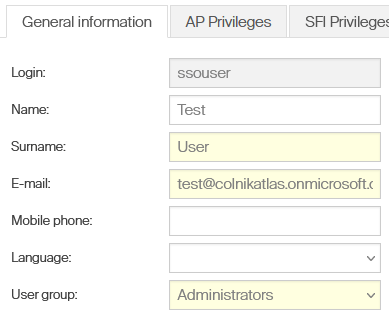

Users from Azure AD cannot access the Admin Portal if there is no related user found in the Portal.
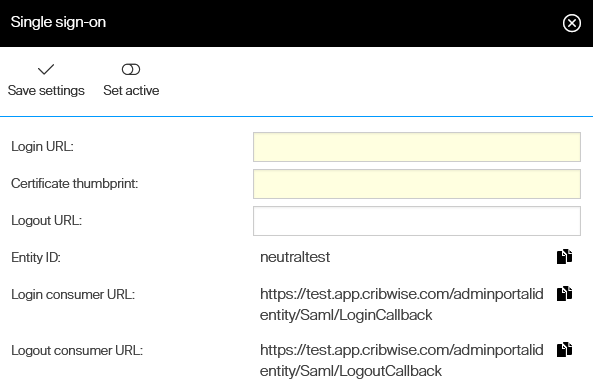
In Admin Portal, Navigate to System settings -> Access control and select Setup SSO. Note information Entity ID, Login consumer URL and Logout consumer URL, which will be set in Azure AD.
In Azure AD, setup new Enterprise application for CRIBWISE. In the Enterprise application detail, select to manage Single sign-on.
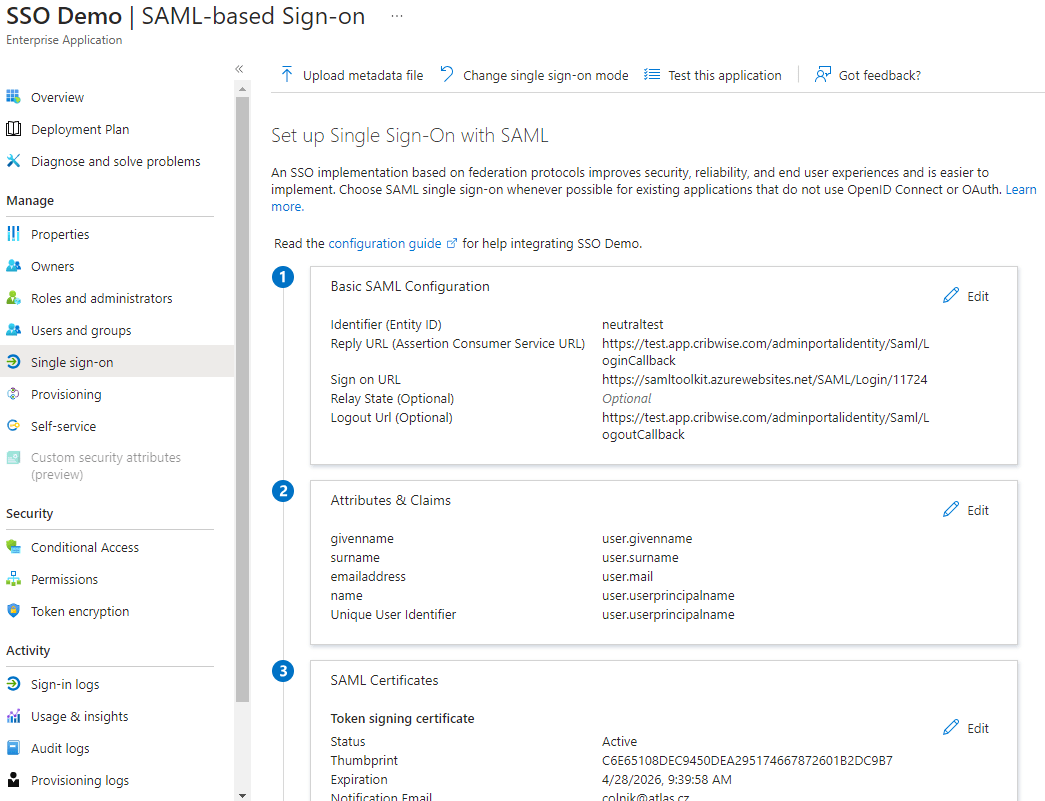
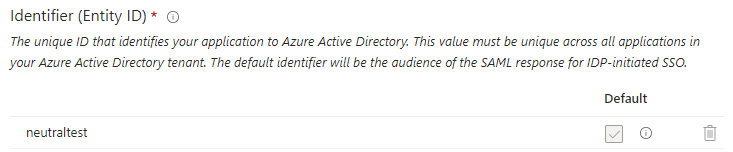
Select to edit Basic SAML Configuration. Set Identifier (Entity ID) to value of Entity ID field, taken from Admin Portal.
Set Reply Url (Assertion Consumer Service URL) to value of Login consumer URL, taken from Admin Portal.
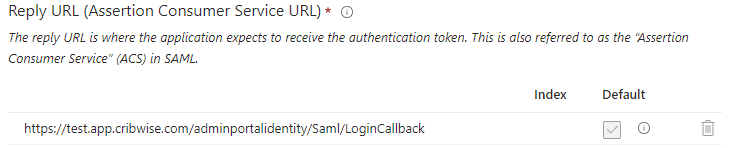
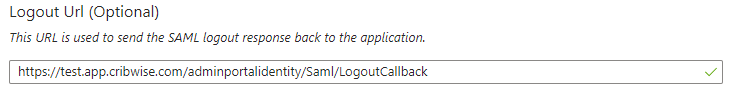
Set Logout Url to value of Logout consumer URL, taken from Admin Portal.
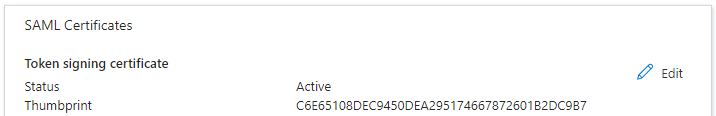
Save the configuration. In SAML Certificates section, locate and note certificate Thumbprint.
In Setup of the application, locate and note Login URL and Logout URL.
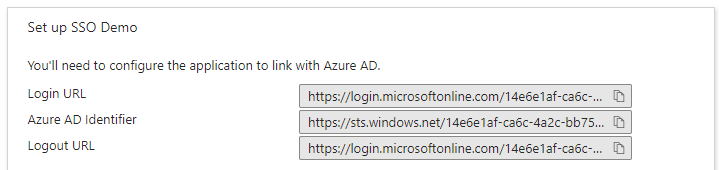
Setup of Azure AD is done. Navigate back to Admin Portal to SSO setup page. Set Login URL to value of Login URL taken from the AD. Set Certificate thumbprint to value of Thumbprint taken from the AD. Set Logout URL to value of Logout URL taken from the AD.
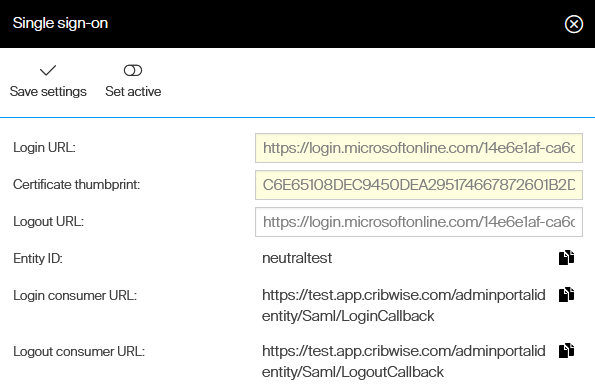
Save settings and press Set active. Portal will validate, if all users in the Portal have unique email address. If not, the SSO is not activated.
Test the SSO before logout.
Once active, it is highly recommended to keep current Admin Portal window opened and open a new browser window in private mode and access the portal.
Opening portal address will redirect to Azure AD login page.
Perform test login to verify if login can be performed properly. In case of any problem, deactivate the SSO in the original window.
While access for account administrators is enabled, it is possible to access the Admin Portal via link from Customer Management Portal even when SSO is active.
Activating the SSO while having access for account administrators disabled may lead to login to Admin Portal is not possible.